
To scan Nmap ports on a remote system, enter the following in the terminal: sudo nmap 192.168.0.1. Replace the IP address with the IP address of the system you’re testing. This is the basic format for Nmap, and it will return information about the ports on that system.
In this tutorial you’ll fined 20 basic examples of Nmap command usage.
Nmap is able to scan all possible ports, but you can also scan specific ports, which will report faster results. See below: nmap -p 80,443 8.8.8.8. Scan multiple IP addresses. Let’s try to scan multiple IP addresses. For this you need to use this syntax: nmap 1.1.1.1 8.8.8.8. You can also scan consecutive IP addresses: nmap -p 1.1.1.1,2,3,4. Also you could use a network tool such as nmap with the option -A, -O, or -sV (Active Fingerprinting and service version) and filter Apple mac addresses prefix using a network anylizer. Looking at the service version, port numbers tcp 65xxx being a iphone-sync port, tcp 548 AFP (OS X) will help you to determine OS X version and Hardware but. You can spoof a MAC address when using Nmap with nothing more than a -spoof-mac command line option for Nmap itself to hide the true source of Nmap probes. If you give it a MAC address argument.
You’ll see how to use Nmap from the Linux command line to find active hosts on a network and scan for the opened ports.
You’ll learn how to determine a remote operation system using TCP/IP stack fingerprinting and how to discover what version of software is running on a remote host.
I’ll also show how to use Nmap for stealthy scanning, how to detect firewalls and spoof MAC address.
Cool Tip: Want to stay anonymous? Learn how to use PROXY on the Linux command line. Read more →
1. Scan a Single Host or an IP Address
Scan a Single IP Address:
Scan a Host Name:
Increase Verbosity Level:
2. Scan Multiply IP Addresses
Scan Multiple IP Addresses:
Scan a Subnet:
Scan a Range of IP Addresses (192.168.1.0 – 192.168.1.200):
3. Scan Network for Active Computers
Cool Tip: Scan the network with the ping command only! Discover all the active computers in your LAN! Read more →
Scan for Active Hosts on a network:
4. Scan a List of Hosts From Input File
Scan hosts/networks from the Input File:
Format of the input file:
5. Exclude IP/Hosts/Networks From Nmap Scan
Exclude Targets from Nmap scan:
Exclude List of hosts from a file:
Format of the exclude file is the same as format of the input file shown above.
Zenmap Mac
6. Scan For Specific Ports
Scan for a Single Port:
Scan for Several Ports:
Scan for a Port Range:
Scan for All Ports:
Scan for top most Common Ports:
7. Determine Supported IP Protocols
Determine which IP Protocols (TCP, UDP, ICMP, etc.) are supported by target host:
8. Scan For TCP/UDP Ports
Scan for All TCP Ports:
Scan for Particular TCP Ports:
Scan for All UDP Ports:
Scan for Particular UDP Ports:
Combine scanning of different ports:
9. Perform a Fast Scan
Nmap Look For Mac Address
Enable Fast Mode:
* Scan fewer ports than the default scan.
10. Display the Reason a Port is in a Particular State
Display the Reason why Nmap thinks that a port is in a particular state:
11. Show Only Open Ports
Show Only Open Ports (or possibly open):
12. OS Detection
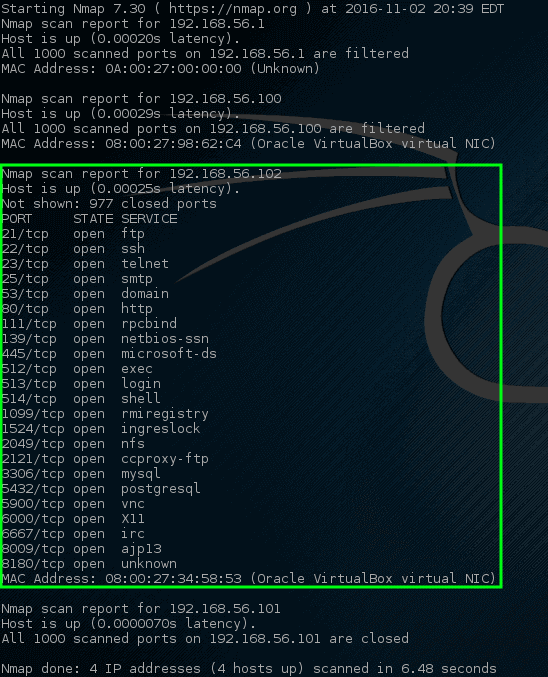
One of Nmap’s best-known features is remote OS detection using TCP/IP stack fingerprinting.Nmap sends a series of TCP and UDP packets to the remote host and examines the responses.
After performing dozens of tests, Nmap compares the results to its database and prints out the OS details if there is a match.

Turn on OS Detection:
13. Service Version Detection
Turn on Version Detection:
* Discover what version of software is running on a remote host.
14. Firewall Detection
Find out if a host is protected by any Packet Filters or Firewall:

15. MAC Address Spoofing
Spoof your MAC Address:
Spoof your MAC Address with a Random MAC:
16. Scan a Firewall For Security Vulnerabilities
These three scan types exploit a subtle loophole in the TCP RFC to differentiate between open and closed ports.When scanning systems compliant with this RFC, any packet not containing SYN, RST, or ACK bits will result in a returned RST if the port is closed and no response at all if the port is open.
As long as none of those three bits are included, any combination of the other three (FIN, PSH, and URG) are OK.
TCP Null Scan:
* Don’t set any bits (TCP flag header is 0).
TCP Fin Scan:
* Set just the TCP FIN bit.
Nmap Get Hostname
TCP Xmas Scan:
* Set the FIN, PSH and URG flags (lighting the packet up like a Christmas tree).
17. Stealthy Scan
Cool Tip: Stay anonymous during port scanning! Use Nmap + Tor + ProxyChains! Safe and easy penetration testing! Read more →
TCP SYN Scan:
* Well known as a half-open scanning, as it doesn’t open a full TCP connection.
18. Disable Host Discovery (No Ping)
Don’t ping host before scanning:
19. Disable DNS Resolution
Cool Tip: Need to improve security of the Linux system? Encrypt DNS traffic and get the protection from DNS spoofing! Read more →
Never do reverse DNS Resolution on the active IP addresses it finds:
20. Save Output of Nmap Scan to a File
Save output of Nmap scan to a TEXT File:
Nmap Ip List
Save output of Nmap scan to an XML File:
